Comodo Silent Installation Switches
Silently install the msi package, no reboot msiexec /i C: setup.msi /qn /norestart Silently install the msi package and write the installation log to file C: msilog.txt. Starting Comodo Endpoint Security (in Comodo Endpoint Security Manager). Silent Mode option.Silent Mode - Switches CES to Silent Mode to enable you to configuring without any interruptions from various alerts in your computer. The operations that can interfere with users' configuration experience are either suppressed or postponed.
One awesome benefit of these events are the tricks and tools we introduce to each other. Focus 25 IT admins on a single topic and you’ll have no choice but to learn something cool.
The coolest thing I learned came from reader Kei Bi. When I first saw it, I couldn’t wait to share it with you!The Problem with EXE Silent SwitchesMost applications aren’t exactly standardized.
Any silent switches that the EXE might support are dependent upon the packaging technology (ex: InstallShield) and the vendor. In our training, we spent a good bit of time talking about the different switches that might make an application install silently.
When unsure, just starting throwing random switches at it!The issue with the above method is that you have to remember a bunch of useless information just to get your application to deploy. In the past, I’ve used two excellent websites to find installer switches: and While I prefer MSI deployments, sometimes you are stuck deploying an EXE. Finding silent switches for these apps can be time consuming. Like most things in IT, there is a better solution.The Ultimate Silent Switch Finder (USSF)First, It is a standalone EXE within a ZIP so you will want to extract the contents.
After launching USSF, select the “” symbol next to File and browse to a setup file. I was working on a new deployment for a DYMO label maker and browsed to its setup file.As you can see in the screenshot below, the DYMO setup is a NSIS package and it uses a /S for a silent switch.
Not to be confused with an NCIS packageI tried out a new application (Camtasia Studio). It turned out to be a Wise Installer than uses a /s for a silent install. Fun fact – these switches can be case sensitive!Next, I tried out an InstallShield package.
In the screenshot below, the /v”/qb” line indicates than an MSI is inside that EXE. We know this because /qb is an MSIEXEC command for a quiet+basic install.I did run across one custom packaged EXE. Because it was a custom app, USSF couldn’t find a silent parameter.
Hopefully, you won’t have too many custom apps like this. Overall, this tool should save you a good bit of time! Thanks again to Kei Bi for bringing it to my attention. Hi J!SFXMaker – another application detect silent switch keys (uses Exeinfo PE – compressor detector) and create SFX archive – but I have not tested.And I often use Universal Extractor special utility for extract exe – analogue 7-zip. I fan portable software 🙂ps for Universal Extractor: “Note that in order for Universal Extractor to operate on installers created using newer versions of InnoSetup, you should download the latest version of innounp, then extract innounp.exe and place it in the bin subfolder of Universal Extractor.”isoft-onlineDOTcomportablefreewareDOTcom/index.php?id=641PS: Apps use is simply.
But it is better to learn and train, so in particular, I read your blog 😉PPS: I’m sorry to translate into English me helped Google.
This guide was written for version 8.0 of Comodo Internet Security (CIS). This guide will work equally well for configuring Comodo Firewall, but the screenshots are from CIS.Please note that in terms of system protection this article is not really meant to be viewed in isolation.
Please read my article about in order to get an overview of what you can do to protect your computer. Comodo Firewall provides rock solid protection and is entirely free. If you like you can even download Comodo Internet Security, which comes with Comodo Antivirus. This is also completely free.Recent Changelog:6/10/2014-Replaced http links with https links wherever possible.9/14/2014-Updated advice to show how to remove messages from COMODO Message Center-Updated article to reflect the newly released CIS version 8.0Index. 1.2.A)B )C)D)3.4.1. InstallationBefore installing security software designed to protect your computer I find it's best to first ensure that your computer is already free of malware.
I know it sounds like strange advice, but this can prevent many problems further down the road. To do this please follow the advice I give in my article about.
Note that, as mentioned in that article, I would advise that you submit all unrecognized files to Comodo to be whitelisted. That article explains how to do this. If all of the files on your computer are whitelisted you will find Comodo Internet Security to be very quiet, except when there is a possible threat.After this is done you can download the installer. Here are the download pages for. Please download whichever you would like to install. If, at a later time, you decide that you want to switch from one to the other you can accomplish this by going to the start menu, finding Comodo, and selecting the option to 'Add and Remove components'.Options During Installation. During installation you will first see a scren which asks you whether you want two options to be enabled.
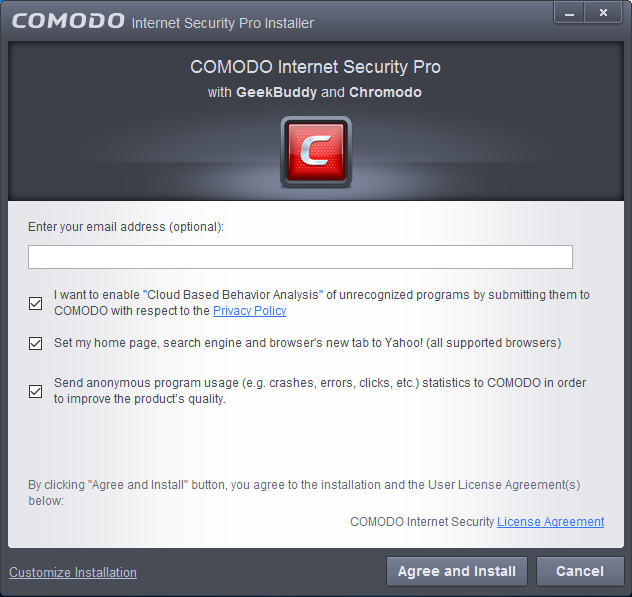
I would recommend leaving the box to 'enable 'Cloud Based Behavior Analysis'.' I would strongly advise that you leave this option checked. This will upload all active unrecognized programs to Comodo for analysis. These files will then either be added to the whitelist or added to the definitions for the antivirus. This will make Comodo Internet Security both easier to use and more powerful against threats. The other box, to 'Send anonymous program usage.' , you can uncheck if you desire, or you can leave it checked. It's entirely up to you.Before going to the next screen select the option in the lower left-corner called 'Customize Installation'.
In addition you should select the small option near the bottom of the window that says 'Customize Installer'. This will give you the option to choose which components, and additional programs, you would like to install. You may wish to consider leaving the option to install checked.
This is a free trial program through which Comodo technicians can remotely diagnose, but not fix, problems with your computer. This trial period will only start once you first use it. If at a later date you decide to purchase the product then the technicians can also remotely fix any problems with your computer. However, if this does not sound useful you can deselect it. Also, if you do choose to install it you can always choose to uninstall it later.You are also given the option to install the browser.
If you do not wish to install this then deselect this option as well. You can also uncheck the option to 'Install PrivDog.' This is an adblocker similar to Adblock Plus. However, it replaces most ads with ads which are verified to be safe, but which may still be able to provide the site you are viewing with some revenue. Personally, I use Adblock Plus, but the choice is yours.
Once you're done, click on Back and then click Next.On the next screen you are given the choice to change your DNS servers to. This will automatically block any websites that Comodo knows to be dangerous. However, I have noticed that Comodo DNS sometimes tends to block legitimate sites. Thus, if you would like to use the security of a secure DNS serverI would recommend following the advice I provide in of my article about How to Stay Safe While Online, or just use the default one from your ISP. Thus, my recommendation would be to uncheck the option in this installer about enabling Comodo Secure DNS. You can also uncheck the option to change your home page and search engine to Yahoo. Leaving it checked will help to support Comodo, but it is very easy to opt out if you do not wish to use Yahoo.
After that you can click 'Agree and Install' and the installation will begin.2. Changes To ConfigurationNot long after the installation is complete, assuming you installed CIS, it will download the virus database and begin running a quick scan of your computer. Let this scan complete. Unless you have a slow internet connection this process should only take about 5-15 minutes. Either way, I would suggest letting it complete its scan. After the initial scan is completed any subsequent scans will be much faster due to Comodo's new caching technology. Once it's done you can close the scan window.
However, note that once you close the scan window it will ask you to restart your computer. Do not yet allow it to restart your computer.At this time you may also choose to disable User Account Control (UAC). Personally I do disable it. However, there are some reasons to leave it enabled. One problem is that disabling this will turn off protected mode in Internet Explorer. It will also disable file/registry virtualization for Windows Vista and Windows 7. In general, UAC controls who can run specified applications that require elevated Administrator privileges. For more information please read.A) General Tweaks To The ConfigurationChange Overall ConfigurationOne of the most important changes it to change the default configuration to Proactive Security. For an explanation of the differences between the configurations please see. To do this open the main window for Comodo Internet Security. Then click on the green task icon on the upper right hand corner of the Window.
This will flip the screen to show you the task window, which contains the configuration options. Click on the section for 'Advanced Tasks' and then select the option to 'Open Advanced Settings'. Make sure the dropdown menu under 'General Settings' is shown and then click on the Configuration option.Now right-click on the option for 'COMODO-Proactive Security' and select Activate. It will ask you whether you want to save changes, but at this point you can select no.
It will then ask you to restart your computer. Make sure you select OK on the Advanced Settings Window. Then, you can either restart your computer now or you can postpone it again and continue making changes.Other General StepsAfter this again open up the main screen for CIS. This time click on the icon on the upper left hand corner of the screen, as shown in the picture to the right, to switch CIS to advanced view.Then click the icon at the bottom of the windows labeled Scan.
Those with CIS installed should select the option to run a 'Rating Scan'. Note that if you did not install the antivirus component clicking on scan will automatically begin running a rating scan.
Find Silent Install Switches
Allow this scan to complete. Unless you have a slow internet connection it should not take more than a few minutes.What this is doing is scanning the critical areas of your computer and compiling a list of which files are already known to be safe, dangerous, or unknown. No action is required on your part as long as you already followed my advice about how to ensure that your computer is not infected. The only reason I ask you to do this now is that it will help make Comodo Internet Security a little bit faster and less resource intensive than it otherwise would have been. Once the rating scan is complete you can close the rating scan window without selecting any action for the files, unless you would like to remove some bad files or trust some unknown files which you know to be safe.Once the scan window is closed please once again look at the main window for CIS. For the section labeled Auto-Sandbox left-click the text next to HIPS which reads 'Safe Mode' and change this to Disabled. My configuration will actually not require you to enable the HIPS.
This version of Comodo Internet Security is designed in such a way that you can achieve the same amount of security without enabling the HIPS. Everything we will need is actually now contained within the Auto-Sandbox, which will provide far fewer popups.Then once again flip the screen to get to the Tasks window. Then go to the section for 'Firewall Tasks' and click on the option for 'Stealth Ports'. In the window which pops up click the option to 'Block Incoming Connections'. Then go to the section for 'Advanced Tasks' and once again click on the icon for 'Open Advanced Settings'.
Under the section named 'User Interface' deselect the box named 'Show messages from COMODO Message Center'. This will prevent CIS from displaying any advertisements. While in this same area you can also choose to disable the sounds which CIS now plays when an alert is shown, if you wish. When you are done select OK to save your changes and close the window. Then leave this window open and continue to the following steps. We will use this window to complete the rest of the changes which will be made to the configuration. I have broken the rest of the advice into that which is applicable for each of the main components of Comodo Internet Security.B) Configure AntivirusAssuming you chose to install Comodo Internet Security you also installed the antivirus component. Please open the Advanced Settings again. Then, make sure the dropdown menus under 'Security Settings' are shown.
Click on the one for Antivirus. Then click on the one for Scans. If you do not want your computer to run scheduled scans you can slide the toggle for both scans to deactivate them. Other than that there are not really any other changes which need to be made to the antivirus component.Also, as strange as this may sound, any scans run from right-clicking on a file or folder use the settings for the Full Scan.
Thus, for example, if you would like for right-click on-demand scans to check all files against the cloud, you should first right-click on Full Scan and choose edit. Then go to the Options section.
Under here you would check the box for 'Use cloud while scanning'. However, do note that making this specific change will make any Full Scans you run take much longer.
You can also make any other changes you like to these settings. Once you are done make sure that you select OK to save the changes.C) Configure Defense+All of the most important changes I would recommend for the Defense+ component have already been made. However, there are some optional changes which you may want to consider.Optional ChangeIf you like you can make sure that Defense+ is selected. Then, under this click on Sandbox and then Sandbox Settings. From this you may choose to disable the option to 'Show privilege elevation alerts for unknown programs'.
What this will do is ensure that the only popups you get are to let you know that an application has been sandboxed. The program will not ask you whether you want to allow an application or not. Thus if you select this option you will not have to answer a single Defense+ alert. Every program, even if it is an installer, will automatically be sandboxed.If this is not disabled running most unknown installers will prompt an unlimited rights popup, which would ask you whether you trust them. However, do note that if sandboxed none of these programs would be installed on the real computer. They would be installed in the fully virtualized environment.
Thus, disabling that option will ensure that you receive fewer alerts, although you will still receive a few from the firewall component, but it will also mean that all unknown programs will always be run in the fully virtualized environment. Thus, I would recommend making this change only if you are an advanced user and are prepared for the consequences.D) Configure FirewallStrongly Recommended ChangesNow open the dropdown menu for the Firewall component. Click on 'Firewall Settings' and check the boxes for 'Filter IPv6 traffic', 'Block fragmented IP traffic', 'Do Protocol Analysis', and 'Enable anti-ARP spoofing'.
Selecting these will likely not have any negative side-affects on your browsing experience. However, if you do find that you are having trouble with your internet/network connections please try unchecking these options as they are likely the culprit. Also, although it's preferable to leave it checked, in some cases the option to 'Filter loopback traffic' may cause certain DNS services to not work correctly. This is rare, but if this happens you can uncheck the option to 'Filter loopback traffic'. However, as long as there are no problems I would advise that you leave it checked.Optional ChangeAlso, if you do not want any unknown programs to be able to access the internet you can check the box for 'Do NOT show popup alerts' and then change the behavior to 'Block Requests'. This will automatically block all unknown applications from accessing the internet. Thus, if you select this option, and the optional one for the Defense+ component, the only popups you will see are those for the sandbox.
Also, note that the sandbox popups do not require any user input. Thus, Comodo Internet Security will now be entirely automated and will require no user input at all.However, making this change to the firewall configuration will cause some unknown programs to not be able to operate correctly and will also result in any unknown installer, which must download files from the internet, failing. Thus, I would recommend making this change only if you are an advanced user and are prepared for the consequences.
Note that if you do run into problems with this change, you should just uncheck the option.When you are done making your changes select OK. This will save all changes and close the advanced settings window.3. Advice On How To Use Comodo Internet SecurityHow To Answer Defense+/Sandbox/Firewall AlertsIn terms of how to use this program it's really quite simple, at least for the most part. The main problem is that although there are very few alerts which you will have to answer, there are still some decisions which will have to be made. For ordinary sandbox alerts no action will be required on your part.
CIS will just show a small popup on the lower right-hand corner of the screen to let you know the application has been sandboxed. However, this popup will provide you with the option to trust the application.For any popups, regardless of which component they are from, it is very important that you do not just allow an application because you want to get rid of the alert. If you do this you greatly decrease the protection offered by Comodo Internet Security. In general, regardless of what the alert is asking, you should only allow a program access to your computer if you are absolutely sure that it is safe.If you're not sure whether an application is safe or not I would advise that before allowing it you take some time to check it by following the advice I give in my article about. However, if you're not sure what to do I would advise that you select the option to block the request or, if it is a sandbox alert, do nothing and leave the application sandboxed. If you do otherwise you may inadvertently allow a malicious program access to your computer.Overview of What Game Mode IsCIS also has an option called 'Game Mode'. If you choose use this no Defense+ alerts, Firewall alerts, update popups, or scheduled scans will be shown or run.
Thus, these cannot interfere with what you are doing. However, what enabling this will also do is create automatic allow rules for all running applications.
Thus, running your computer in game mode will essentially put your computer in training mode, which I would not advise as I consider it to be dangerous. Thus, I would advise that you do not use 'Game Mode'.Brief Overview of How the Auto-Sandbox WorksAlso, I would quickly like to briefly mention the way in which Comodo's sandbox component works.
If a piece of malware is not yet detected as dangerous by Comodo it will automatically be sandboxed. When in the sandbox it may be run in a fully virtualized environment where it is not able to harm, or affect, the real system.Overview of Comodo Virtual DesktopComodo Virtual Desktop creates a fully virtualized environment on your computer.
It can be accessed by going to the tasks window, going to the 'Sandbox Tasks' section, and clicking on 'Run Virtual Desktop'. This starts the fully virtualized environment which is mainly meant to be used for web related activities. It is not really designed for installing other programs, although many programs will install correctly inside of it. In addition, any programs which are installed on your real computer, and have a shortcut sitting on the desktop, will be able to be launched from inside the Virtual Desktop. However, note that in order to access them you will need to switch from the tablet screen to the desktop screen. This is done by flipping the window by clicking on the orange icon, just as you would with the CIS window.Also, please do be aware that due to restrictions, which help protect you from dangerous malware, there are certain types of programs which will not be able to run inside the Virtual Desktop.
Also, note that if the Virtual Desktop is closed and then started again no applications will initially be running. This would include any malware which may have been running. Thus, I would recommend that before performing sensitive actions such as online banking you at least close the Virtual Desktop and then open it again just before you go to the banking site.
If you like you can even choose the option to 'Reset Sandbox', which will delete all information which was inside it and provide you with an entirely fresh sandbox the next time you run the Virtual Desktop.Also, the shared space folder, of which a shortcut is placed on your desktop during installation and an icon is placed in the main window for CIS, is the folder which is shared by both your actual computer and the Comodo Virtual Desktop. Thus, any files placed in there will be shared between the two environments.Optional Cosmetic ChangesIf you would like to run your browser sandboxed, but would prefer not to use the Virtual Desktop, you can instead use the widget. This is the small window which has been added to your desktop. This will automatically detect and display all browsers currently installed on your computer, along with other useful information. Clicking on the icon for that browser will cause it to be run sandboxed with full-virtualization. Note that you can also right-click on the CIS icon and either add or remove information from the widget.Please note that any changes you make to the browser while sandboxed, such as bookmarking a page, will not be saved to your unsandboxed browser and will in fact be deleted when you reset the sandbox. Note that if you do not want to use the widget you can remove it by right-clicking on the CIS icon, selecting Widget, and unchecking the option to Show.
Personally, I use it often, but if you find it an eyesore it is easy to remove.If you like you can also open the Advanced Settings again. Then, under General Settings make sure that User Interface is selected. In this area you can choose between different themes which come with CIS.
From here you can choose the Theme which suits you best.The main window of Comodo Internet Security also provides you with the option to add task shortcuts to the task bar at the bottom of the window. To add additional task shortcuts you can flip the screen to the task window, navigate to the task you want to make a shortcut of, right click on the icon for it, and select 'Add to Task Bar'. I would suggest you do this for any tasks which you find you are using often. Note that you are also given the ability to drag the icons around on the main window.4. What To Do If You Have Further QuestionsNote that if at any time after installing this product you encounter serious problems with it, which running the diagnostics cannot fix, it may be helpful to reinstall it. If you do decide to reinstall Comodo Internet Security it's best to do this by following the steps I outline in my post on.If you do have any other questions please peruse the online help files, which can be found on.
If you still have questions then I would advise that you search the for a solution. If someone hasn't already created a post with the same problem please feel free to join the forum and create a post of your own. The community will do their best to help you with any problems that you may encounter.Please help. Also, if you believe this article deserves anything less than 5 stars, please leave a comment below explaining how you think it can be improved or where you find fault. This article is written by me but fueled by the community.
Thus your opinions and advice are not only much appreciated, but actually necessary in order for this article to grow and improve.If you found this article useful then perhaps you'd like to check out some my others.This software category is in need of an editor. If you would like to give something back to the freeware community by taking it over, check out for more details. You can then contact us from that page or byPlease rate this article. This is a quote from CIS Help webpage:' Stealthing a port effectively makes it invisible to a port scan.
This differs from simply ‘closing’ a port as NO response is given to any connection attempts (‘closed’ ports respond with a ‘closed’ reply- revealing to the hacker that there is actually a PC in existence.) This provides an extremely high level of security to your PC. 'I am rather a newbie so I want to ask you if is it really necessary to use “Stealth Ports” option when the computer is used only at home and it is placed behind NAT router that passes the ShieldsUP!
I read that enabling this option may cause problems with some network activity like P2P. Or maybe this doesn’t matter and you recommend to stealth ports anyway?. or to post comments.
I've just updated this article to reflect the newest version of CIS which has been released. However, as of this moment it can only be downloaded from a topic on the Comodo forum (found here):That said, it should be available through the main website soon, and I expect that within the next few weeks it will probably be pushed out (as an optional update) to those currently running a previous version.Let me know what you think of my advice, and if you have any questions.Thank you. or to post comments. Gee, Chiron, you replied before I had a chance to edit my comment!
In addition to the name change, I wanted to ask you a question.In CIS 7.0, you suggested users, under the Behavior Blocker component in Advanced Settings, change 'Auto-Sandbox unknown applications' from 'Partially Limited' to 'Untrusted'. Now, in CIS 8.0,under Sandbox, Auto-Sandbox, there are three separate rules.
Do you recommend that users 'Enable Auto-Sandbox' and enable all three rules? Based on your CIS 7.0 recommendations, I assume you do.Thanks again for all your help!!. or to post comments. You are correct in saying that this is normal.
However, I do not know of a way to not log those events. Also, I know that you can configure CIS to allow access, by adding the file to the Behavioral Blocker exclusions, or perhaps it was Shellcode Injection exclusions. Sorry, I can't remember off the top of my head which of the two. However, as this is cmdagent I'm not sure if it will work.You can give it a try though and let me know if it works.
If it doesn't then I'm sorry, but I don't have any other thoughts. Your best bet would be to create a new topic on the Comodo forums and ask for advice. Perhaps someone will know more than I.Thank you.
or to post comments. I thought about it myself to add Process Explorer to the exceptions, so that it is allowed to access the memory of cmdagent.exe, but I'm not sure it is a good idea.This would disable the self protection of CIS (against the process I choose; ProcXp in this case), which seems possible, but it really should not be.I think even a trusted process should not manipulate CIS, the program which is responsible for the security of the system. What if ProcXp gets compromised somehow?With a little social engineering, a less knowledgeable user could also be tricked into allowing some malware process to hack into CIS.As I see the only solution would be to exclude this event from being logged, which does not seem possible, or create a separate log for self protection events.I will ask at the Comodo forums as well. or to post comments. This seems like a great article for the installation, but after trying to follow it, I realised that the Anti-virus part has not installed.I assumed it had, as it told me I had a successful installation, but since I don't see the ' Anti-Virus' sections, I conclude it hasn't.I would have to agree with a comment that the installation process is among the worst I have experienced. First, I want to know whether you are able to access the internet at all. For example, are you able to open a browser on the computer and use Google?
If so then the internet connection has not been affected.Assuming the internet connection is working correctly, then the best way to add the antivirus component is to go to the start menu, find Comodo, and select the option to 'Add and Remove components'. This will have an option to add the Antivirus component. Trying to run an additional installer over the installation will often either not work or cause other problems.Let me know if that works correctly for you.Thanks. or to post comments. Hi,No, I had no internet access: the actual error was that my IP address could not be set or renewed ( I am on wifi using DHCP ).I have resolved this, effectively by un-installing and re-installing.The un-install was very painful, since windows did not recognise that Comodo was installed, and commodo did not have an un-install option. Chiron,Thanks for an awesome guide.Only problem I've had with Comodo is the Virtual Kiosk; I've never been able to get it run properly in either v6 or v7.
Clicking it typically causes a system hang after a short period, especially if I then attempt to open a browser.Configuration:-Win7 Home Premium x64 machine-Comodo Firewall only; MSE is the antivirus.-Your recommended firewall/behavioral blocker/HIPS/etc. Settings-Comodo diagnostics fails to find a problem with the installation.Is the antivirus required to run the virtual kiosk, or do you think some other bug is at work here?Thanks for your time!. or to post comments.